Smart access & visitor control
Verify identities, purpose, and approvals long before anyone reaches your siteSmart access and visitor control gives organization the visibility, verification, and control needed to protect high-security environments without adding friction for guests. Every arrival is authenticated. Every access decision is documented. And every visitor moves through your workplace confidently, backed by risk-adaptive intelligence that quietly does the heavy lifting.

Trusted by world-leading organizations

The new standard for visitor and access control

The old approach
Crowded lobbies, paper logs, and manual ID checks. Limited visibility into who’s entering - and why. Gaps hidden behind processes that haven’t kept pace with today’s security expectations.
The Visitor Management 2.0 approach
Visitors are verified in advance, access is enforced automatically, and hosts are alerted immediately. Your team gets clear oversight and compliance-ready records, and guests experience a secure, professional check-in.Security intelligence operates in the background - strengthening protection while keeping the welcome professional.
A smarter, safer way to manage access control
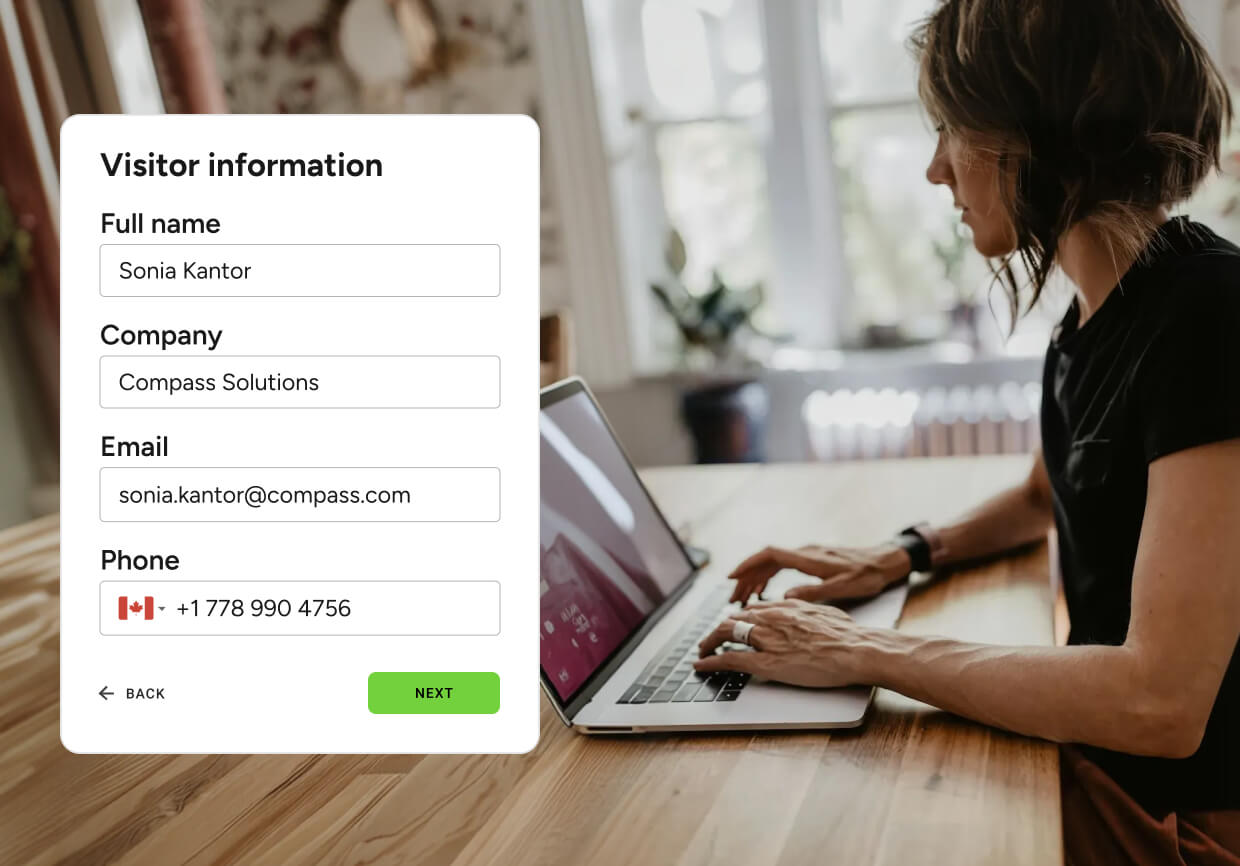
Intelligent pre-arrival verification
Strengthen security before visitors reach your site.
- Pre-screen individuals against internal rules and risk criteria
- Collect and verify documentation in advance
- Alert hosts to required approvals or actions
- Ensure visitors move through check-in quickly upon arrival
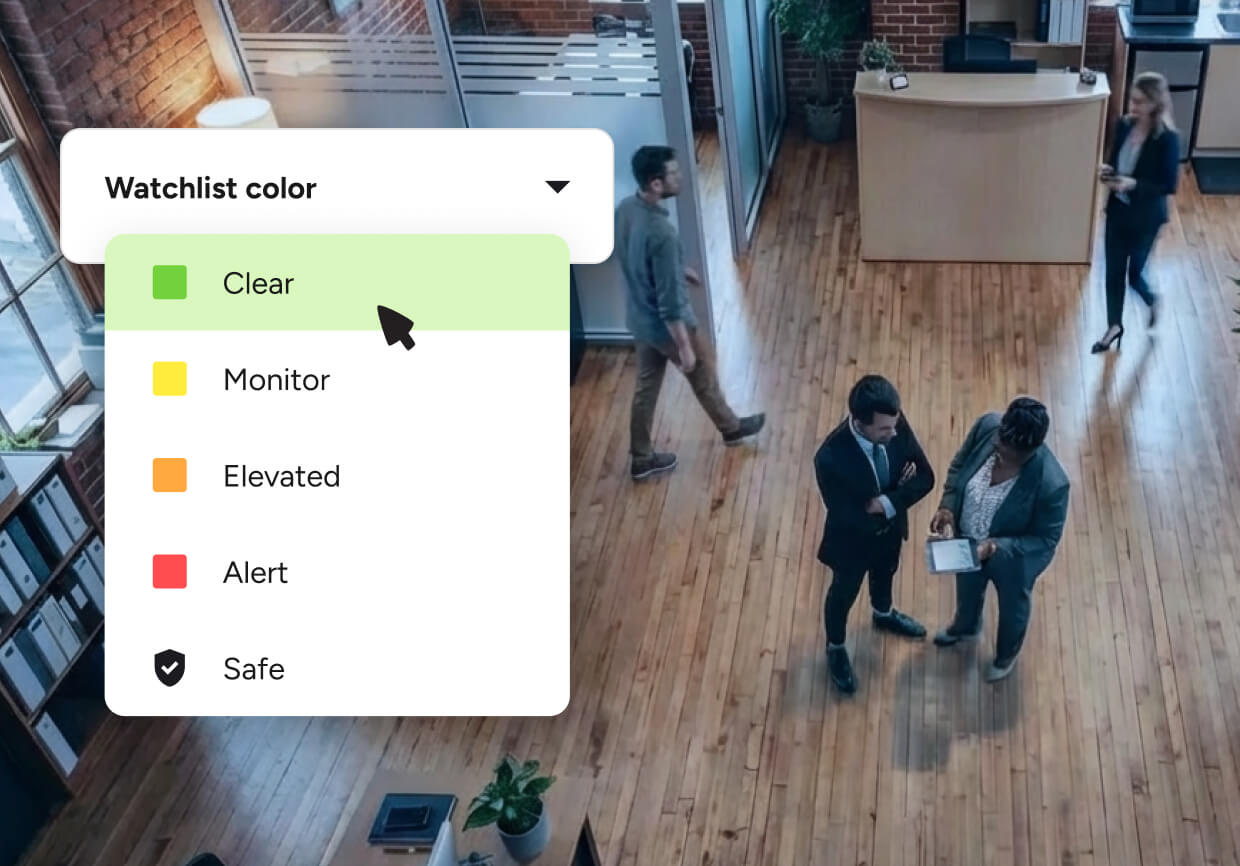
Real-time risk awareness
Stay ahead of threats without slowing operations.
- Automated watchlist and risk screening behind the scenes
- Real-time alerts for anomalies or restricted individuals
- Escalations routed to the right teams instantly
- A continuously evolving view of risk across all locations
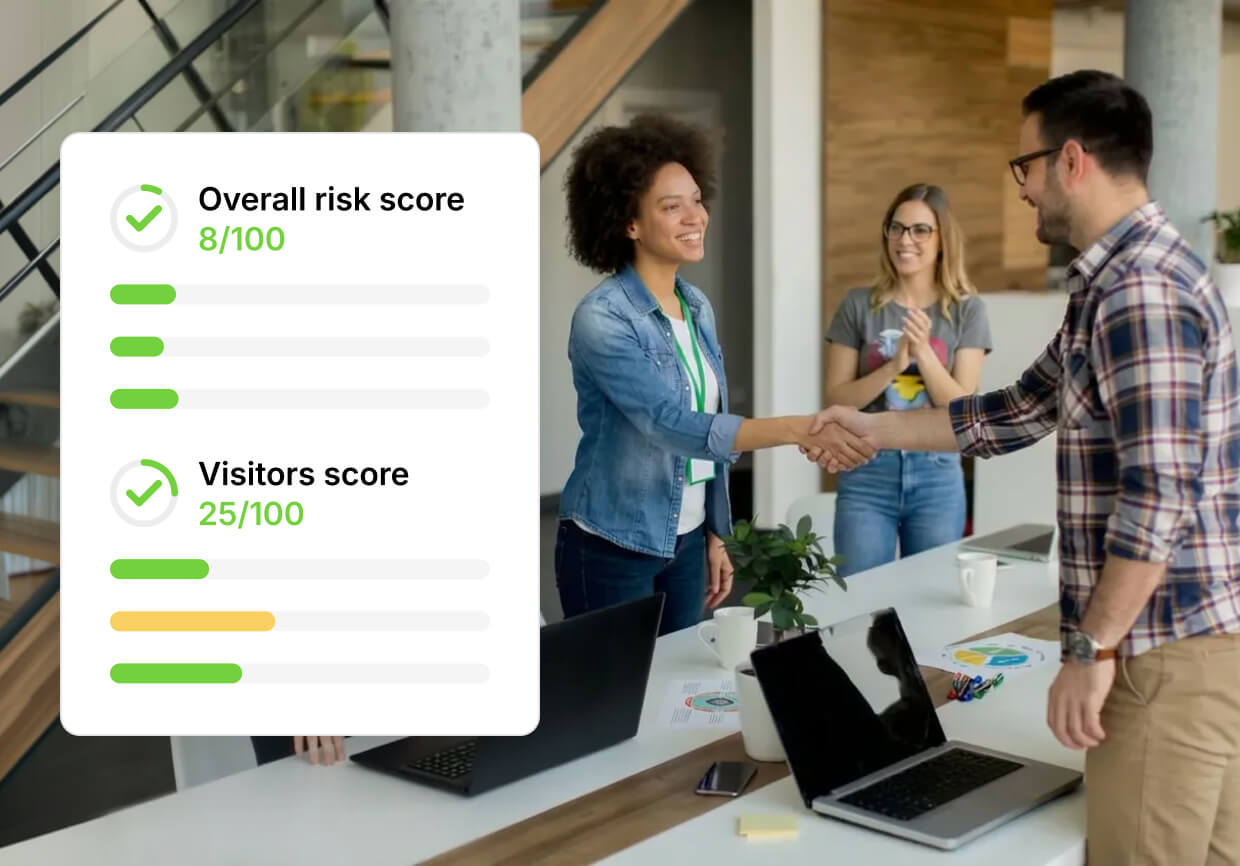
Identity intelligence & audit-ready records
Build trust through precision and transparency.
- Recognize returning visitors, contractors, and partners instantly
- Tailor access pathways by role, purpose, or site
- Maintain full digital trails for compliance, audits, and incident review
- Adapt access rules automatically as risks evolve
The paper log book was impossible to audit. Sign In Solutions takes the pressure off the receptionist. The whole visitor experience has become a lot more fluid.
Smart access in action
Before the visit
- Pre-registration and automated screening
- Risk insights and documentation review
- Advance messaging and clear arrival instructions
During the visit
- Mobile, kiosk, or QR sign-in
- ID verification and badge printing
- Custom visitor flows and policy attestation
- Automated host notifications
Identity & access management
- Role-based access controls
- Credential validation
- Integrations with identity ecosystems (SSO, workforce tools)
Emergency & oversight
- Instant emergency alerts
- Live presence dashboards
- Multi-site visibility and coordination
Designed for regulated, high-compliance environments
Aerospace & defence
Secure access for cleared and uncleared personnel, audit-ready documentation, and risk scoring aligned to stringent regulations.Read more
Government & public sector
Identity verification, policy enforcement, and full accountability across departments, agencies, and shared facilities.Read more
Pharmaceuticals & life sciences
Control movement across labs, cleanrooms, and production sites with accurate records and GxP-aware compliance workflows.Read more
Manufacturing
High-volume contractor oversight, standardized protocols, and instant visibility across sprawling campuses.Read more
Technology and R&D
Protection for IP, secure lab and data environments, and controlled access across hybrid and distributed teams.Read more
Reliable results at every scale
Stronger protection
 Automated screening, real-time alerts, and unified watchlist intelligence reduce exposure across all sites.
Automated screening, real-time alerts, and unified watchlist intelligence reduce exposure across all sites.A more controlled experience
 Fast, guided sign-in paired with automated approvals - no queues, no confusion.
Fast, guided sign-in paired with automated approvals - no queues, no confusion.Reliable performance at scale
 Instant recognition of returning visitors, consistently verified identities, and audit-ready records for every arrival.
Instant recognition of returning visitors, consistently verified identities, and audit-ready records for every arrival.Frequently asked questions
Turn secure arrivals into a strategic advantage
With Smart Access & Visitor Control, security becomes proactive, experience becomes seamless, and every sign-in becomes a moment of assurance.
Talk to us